Dr. Ioannis Savidis, associate professor in the Department of Electrical and Computer Engineering (ECE), is explaining an aspect of the computer hardware security research he has been pursuing for five years now. His recent federal grants have been awarded primarily for obfuscation—security techniques for integrated circuits (ICs) that work just like they sound: they muddy the waters for those who want to find out how a circuit is put together so they can hijack its data or steal its critical intellectual property.

Dr. Ioannis Savidis
But hardware security is a complex matter, and a drift of related issues converge. Hardware Trojans. Meltdown and Spectre and SAT attacks. Fabrication plants. Recycled circuits. Reverse engineering. Cloning. Keys. Gates. It’s fairly complicated stuff for the average laptop user. It’s essential protection for industry and the military. And if it sounds a bit cloak-and-daggerish, it is. Secure hardware, specifically for integrated circuits, is a global challenge with ramifications for everyone reliant on computer technology. Which by this point is nearly all of us.
Savidis’ research confronts the challenge of security in a cyber landscape where the ability to crack circuits and gain access to their internal structure—by competing companies or adversarial nation-states—is increasing. He develops techniques that provide clients with the means to protect their most sensitive intellectual property.
The importance of the research can’t be overstated. Savidis’ lab, the Integrated Circuits and Electronics (ICE) Design and Analysis Laboratory, is supported by a suite of grants from the Air Force Research Laboratory, the Department of Energy, and the Office of Naval Research, as well as a 2018 National Science Foundation CAREER grant awarded last year. Each targets different aspects of the larger problem. But in a world where our most precious information is wired, they all dovetail with the universal need for circuit security.
“We live in an age where the data that’s going through any of these circuits is almost always critical, whether you’re looking at banking information, control of critical systems, or military data. There has always been a lot of work on the software side to prevent data leakage,” said Savidis. “But too often, we’ve ignored the hardware as we’ve assumed that hardware is relatively secure. But it isn’t.”
“During my first year at Drexel, I started seeing all these papers on threats to digital circuits, anything from counterfeiting to reverse engineering. So, I started getting interested in techniques to prevent these attacks. That’s what started me on this research trip. It’s a big puzzle to come up with ways to protect circuits while an adversary is doing all that is possible to crack them. It’s a really interesting problem to work on.”
This year, Savidis will have eight graduate students busy in his lab. Potential students contact him regularly to see how they can be slotted into the program.
“Most students come in not thinking of security as a component of circuit design,” says Savidis. “There’s a lot of interest in how do I design an IC, how do I properly design the power and the clock delivery, which are critical components. And then, I come in and add this extra aspect of security to the list of circuit design parameters—we have power, we have performance, we have area, and now we add security as an additional constraint.
“Among students, there’s a lot of interest in the work. It’s a combination of the problem being important to the DoD or DARPA, for instance, as well as learning something completely new in circuit design. If you look at DARPA, they’ve had multiple project calls on the topic in the last five or six years for different aspects of security. They have also pursued an area that I’m most interested in—how do you include security at design time.”
IC Vulnerabilities
In general, obfuscation seeks to protect an IC by hiding its functionality. Solutions like split manufacturing, IC camouflaging, and logic encryption are techniques in the obfuscation quiver. Savidis’ research focuses on a set of techniques that work in the digital domain—combinational and sequential logic obfuscation—and a set that works in the analog domain—parameter obfuscation.
Unlike software—for which most users get monthly updates to protect against vulnerabilities—physical aspects of ICs are very difficult to modify once they are out of production. So it’s important to bake security into the design process from the very beginning. This is another aspect of Savidis’ work.
Twenty years ago, companies providing electronic components for military and commercial use produced their own ICs through a vertical fabrication process that gave them control of the entire design, fabrication, and validation/test flow. Work that was done on ICs in-house by IBM or AMD, for instance, was secure because the company’s own hardware engineers were fabricating and testing the circuits. But as the technology moved from one generation to the next and the complexity of producing cutting-edge circuits accelerated, fabrication has become significantly more expensive.
Circuits are packed with tiny devices called transistors that communicate with each other to implement computing functions. There can be as many as four to five billion transistors on one integrated circuit. It’s intricate, highly skilled work essentially done for computers by computers. So companies like Apple, Google, Qualcomm, AMD, and Microsoft started outsourcing fabrication, paying large foundry facilities to do this work for them. That reduces costs. But it also invites third-party entities into the process that could tease out the entire design of the circuit, exposing its data to IP theft or piracy, thus reducing years of work and investment by companies to a lead time so narrow that it’s difficult for them to establish commercial viability.
“It’s a big puzzle to come up with ways to protect circuits while an adversary is doing all that is possible to crack them. It’s a really interesting problem to work on.”
Dr. Ioannis Savidis
“With these foundries, you have another entity that’s producing your circuits; or with third-party IP vendors, you are integrating circuit components not designed by you. And the concern there is, you have modifications to the circuit that you are not aware of. They add something in, they pull something out, so you get back something that was not completely designed by you,” says Savidis.
There are other vulnerabilities, too. For example, circuits that reach the end of their natural lifecycles are often recycled, their boards stripped and the building blocks of the circuit returned into the production loop to be used again. This opens a path to reusing ICs in critical systems such as airplanes or telecommunication satellites that, due to aging, do not behave as initially designed.
Still another concern has emerged in the form of attacks that can unlock a circuit’s design in short order. For example, the powerful SAT attack discovered a few years ago can quickly and efficiently crack an IC’s functionality even with some logic obfuscating techniques in place.
Finally, adding security features is an expense that many companies relegate to a lower priority than other parameters of the IC. To get around this issue, Savidis’ research seeks to bake security into the initial IC design with the lowest possible cost to IC area, power, and performance as well as the overall production cost.
Obfuscation is the Key (and requires one, too)
The obfuscation techniques Savidis develops are based on a key combination that unlocks the functionality of a circuit. If you don’t have the right key, the circuit will behave in unexpected ways, rendering it virtually useless to someone trying to pirate it.
On the digital side, for example, Savidis focuses on the logical gates and sequential logic of an integrated circuit. Removing these gates during the design process and replacing them with gates that require a key combination permitting certain functionalities is one way to protect them. Without that key, the IC will still produce logical outputs, but the behaviors will be compromised.
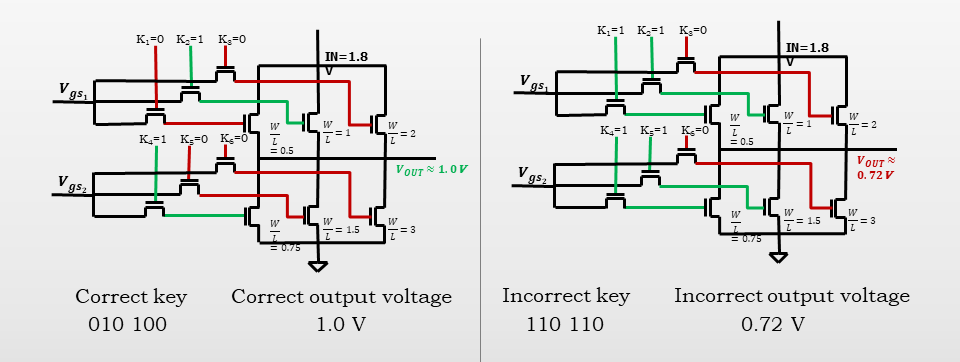
Implementation of Vector-Based Obfuscation Technique – Voltage Divider
Dr. Savidis describes the technique pictured here.
“On the digital side, our techniques result in output corruption,” he explains. “What that means is that your circuits are pretty much useless if you don’t have the correct key. It doesn’t produce the values that you’re expecting it to produce.
“On the analog side, it’s a little bit different—if you have an amplifier and you have a certain gain and a certain bandwidth that you are targeting, and if your keys are not set correctly, they shift your gain and bandwidth, which has the same general effect of rendering the circuit useless.”
Ideally, Savidis can make the security features both more effective and less costly to implement and prevent them from negatively impacting other IC parameters that are essential for commercial viability: power, performance, and area. Research deliverables on his grants will include a series of papers detailing the obfuscation techniques being advanced in his lab. Two journal papers and four conference papers are currently under review.
In addition, he’ll deliver a fabricated IC locked and ready for testing by funding partners to see if it can be cracked.
“And if it is cracked, then we can go back and make modifications and tweak the security techniques to further enhance them,” says Savidis.
Savidis is realistic when asked if data will ever be secure in the cat-and-mouse game of piracy and IP theft. The number of factors that play on each other coupled with the shifting adversarial landscape almost certainly assures that engineers like Savidis will be kept busy researching these matters for a very long time.
“What I’m going to do is make it as costly as possible so that I can protect against, say, 97% of the adversaries out there,” says Savidis. “You might not be able to do that entirely with nation-states that have the resources; there’s always going to be that 3% that will potentially get to it. But if I make it costly enough, that’s a deterrent for most. That’s great. I did my job.”